Cybersecurity Incident Response Report Template - This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected? The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. (e.g., user report, monitoring system alert) detailed description of the incident (include what.
(e.g., user report, monitoring system alert) detailed description of the incident (include what. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected? The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents.
The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. How was the incident detected? (e.g., user report, monitoring system alert) detailed description of the incident (include what. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and.
Cyber Security Incident Report Template in Word, PDF, Google Docs
(e.g., user report, monitoring system alert) detailed description of the incident (include what. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected? The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents.
Cybersecurity Incident Response Report Template
How was the incident detected? (e.g., user report, monitoring system alert) detailed description of the incident (include what. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and.
Free Cybersecurity Incident Response Plan Template Develop Your Plan
The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. (e.g., user report, monitoring system alert) detailed description of the incident (include what. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected?
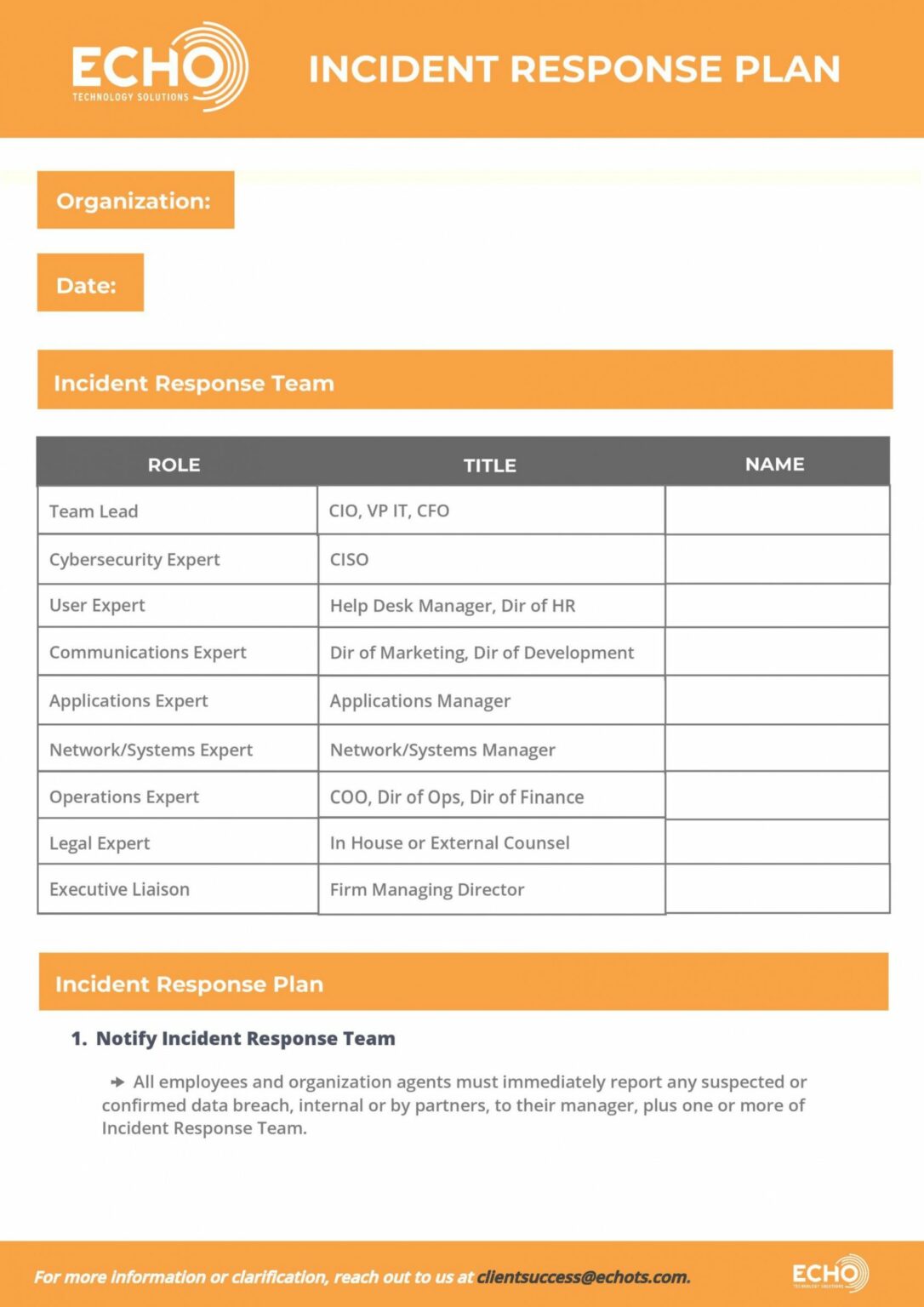
Cyber Security Incident Response Plan Template
This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected? (e.g., user report, monitoring system alert) detailed description of the incident (include what. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents.
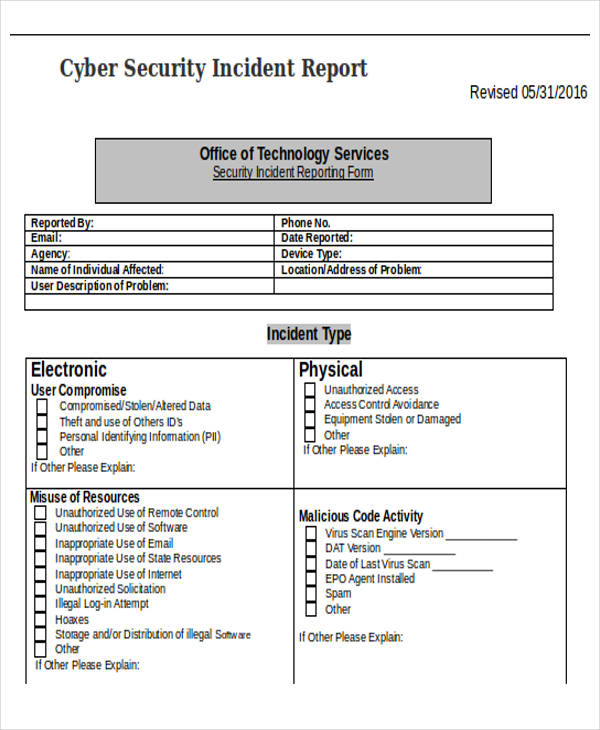
Cyber Security Incident Report template Gratis
(e.g., user report, monitoring system alert) detailed description of the incident (include what. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected?
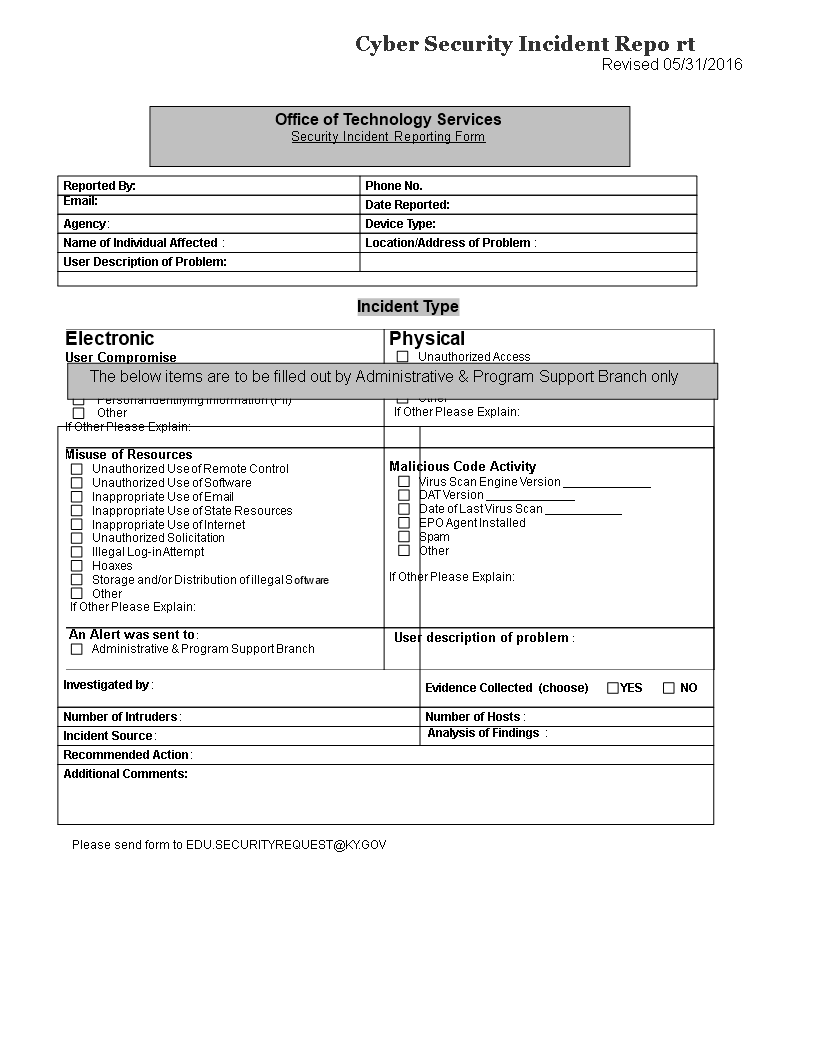
Free Cybersecurity (IT) Incident Report Template PDF Word eForms
This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected? (e.g., user report, monitoring system alert) detailed description of the incident (include what. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents.
39+ Incident Report Templates in Word
How was the incident detected? This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. (e.g., user report, monitoring system alert) detailed description of the incident (include what.
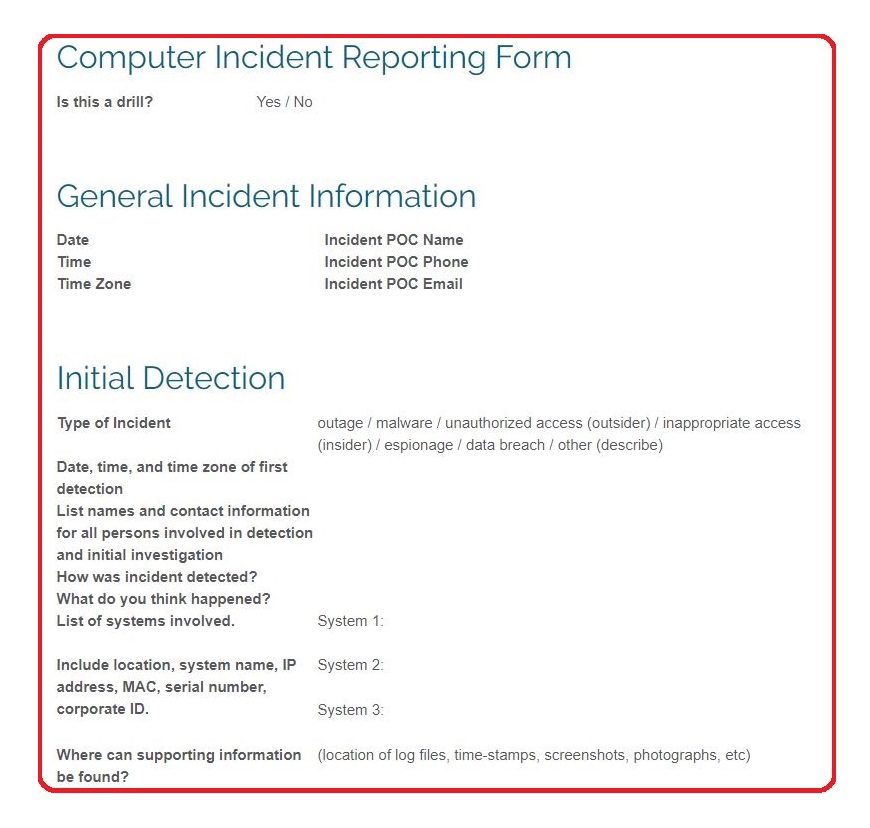
Best Free Computer Incident Response Templates and Scenarios
This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. (e.g., user report, monitoring system alert) detailed description of the incident (include what. How was the incident detected?
A Report Template for Incident Response
This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. (e.g., user report, monitoring system alert) detailed description of the incident (include what. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. How was the incident detected?
Cyber Incident Report Template
How was the incident detected? This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. The cybersecurity incident report template from template.net is ideal for documenting security breaches and incidents. (e.g., user report, monitoring system alert) detailed description of the incident (include what.
The Cybersecurity Incident Report Template From Template.net Is Ideal For Documenting Security Breaches And Incidents.
(e.g., user report, monitoring system alert) detailed description of the incident (include what. This incident response plan template has been derived from the public domain information of the sans institute cybersecurity sample policies and. How was the incident detected?